Unexpected events happen every day. You can prevent “unexpected” from turning into “catastrophic” with planning and preparation. Having a hacking response plan before disaster strikes is the first step to managing a crisis and protecting your business. Generate a recovery plan for hacking events to prevent impact to your business.
Don’t let a hack interrupt your operations. These 6 steps will help you create the perfect hacking response plan to keep your business up and running.
Step 1: Get management buy-in
Hacking Events can cripple or even sink a business. No one person can successfully predict, mitigate and restore function for an entire business. It takes a team and having buy-in from the top makes sure everyone on the team takes it seriously.
It is management’s responsibility to make sure the team has the resources needed to keep systems running. They are also responsible for making sure everyone on the team has the right training and skills to carry out their roles. Finally, you’ll need them to review and approve the plan once created.
Cyber Security is a CEO/Owner level problem and deserves attention by all business stakeholders. The Securities Exchange Commission (SEC) released a report back in 2015 and the problem has only gotten worse. It needs to be a directive, from the top, to generate a recovery plan for hacking events.
Small and Medium businesses are a high-value target for hackers (43% of all Cyber Attacks are on this segment). They are “Easy” or “Soft” targets because they tend to lack a plan, internal staff, and have often have relied on IT professionals who are not trained in Cyber Security to provide guidance. What other business role would you seek advice from someone with no training on the topic?

Step 2: Understand the risks
A recent report by McAfee estimated that a quarter of the data stored in the cloud is the kind that could significantly damage a company or its reputation if lost or stolen.
Cyber-threats are a serious danger to any business. More and more data is stored digitally and that incurs a different set of risks. Additionally, every business has threats that are unique to their industry and location. Here is a summary of 2019 methods used.
Many small and medium businesses fail in 6 months (up to 60% in some reports) and it’s safe to say they did not generate a recovery plan for hacking events.
Create a list of all the potential risks that could impact your business. Identifying these risks is an important step to creating a plan to protect against them.
Step 3: Take inventory of your assets
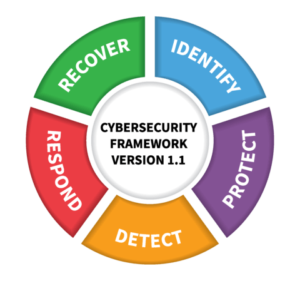
The NIST CyberSecurity Framework
Create an inventory of your company’s assets including hardware, endpoints, software, and configurations. It all matters. Start with your obvious IT hardware (server room) and move outward to users. Don’t forget assets stored offsite (like servers for web/data management) or at secondary business locations.
You need to know what can fail, but you also need to know what will be required to restore function. This list will be the basis of your analysis below. This is critical to generate a recovery plan for hacking events.

Step 4: Estimate the cost of downtime
Now that you have an inventory, evaluate each part of the system to understand what its downtime could cost your business. This will help guide you in the choices you make about your recovery plan. The focus needs to be on items which have a high risk of disruption to your business.
Business Impact Analysis (BIA) is a useful tool that breaks the broad term “downtime cost” into manageable categories. A typical BIA has the following categories:
- Timing of the event
- Duration
- Operational impacts
- Financial impacts
Use this or other rubrics to walk through the business inventory you created. Once complete, you can move on to determine the priorities that are unique to your business. For example, your VoIP phone lines being down may hurt sales and internal communication for a short time, but that downtime may be less important than losing your entire sales database. You can redirect phone lines quickly but you cannot recreate a database quickly! This will define the scope as you generate a recovery plan for hacking events.
Step 5: Determine responsibilities
Speed is vital for responding to a disaster. That’s why everyone should know and understand their roles before a problem arises. Facilities, customer service, and employees can all be impacted by a disaster, so they should all know how to act when crisis strikes. You’ll also need to coordinate with any external partners.
It’s tempting to think that a managed IT solution should handle everything, but your company still needs a plan to interact with your IT service provider and other key members of your team to keep downtime to a minimum.
Step 6: Document and communicate
Now that you have completed the steps above, it’s time to generate the actual disaster recovery plan. A good plan should include all the details decided above about who needs to do what and how to communicate with key staff during recovery. This step will be unique to each company, so document everything in a way that works best for you. There are many resources available such as the NIST CyberSecurity Framework which you can use to develop this plan. To assure success, however, we recommend you work with a CyberSecurity provider and have them guide you through the process. It will happen quicker, the result will be better, and it assures the project completes in a timely manner.
Step 7: Test, practice, and update
You now have a plan, but you’re not done yet. A good disaster recovery plan should be tested often enough to make sure that it remains up to date.
Security tests can be handled by your managed IT service provider but there are other internal ways to test and practice, such as employee notification services and off-hours tests. Additionally, just because your data is stored offsite, doesn’t automatically mean it’s safe. Talk to your data backup provider to ask about their backup plan to make sure your data is kept intact and reliable with regular tests.
When systems change or new employees arrive, the plan should be reviewed and updated as necessary. Even if there are no changes, the plan should be reviewed annually, at a minimum.
The best plan for you
The worst plan is no plan. Don’t wait until it’s too late. By following the steps above you can create a disaster recovery plan that will work for your business. Take stock of your assets, your data, and your risks. Document who is responsible, what needs to be done, and when they need to do it.
Feeling overwhelmed? Contact your managed IT services provider for help developing a foolproof plan to keep your business running.



